The Classic Start Menu, the only component I use from the whole suite, of ClassicShell simply rocks. You could say it makes Windows 8 and beyond, as well as the corresponding server versions, usable at all. Remember? MS was so “kind” to remove the beloved start menu and start button. Not only had the start menu gone through some ugly incarnations ever since Windows XP , since Windows 8 it was completely gone. In general some of the improvements could be considered as an utterly friendly British “up your a…” with a nice English accent. Hint: quick launch was much more than pinning programs to the task bar and I’ll not sit in front of a PC all day long and touch its screen in order to do my work. Or to put it more succinctly: table != pc.
I loved me the proper classic start menu and button!
Anyway, the Classic Shell Start menu button apparently infringed on MS’ rights to their Windows brand. So the release history shows for version 3.6.8:
Version 3.6.8 general release (Jun, 2013):
[…]
Modified the Classic Shell logo and removed the Metro button by request from Microsoft
I don’t like the new button. The author of ClassicShell may be a great programmer, but he ain’t a great graphics designer. And regardless, even if he was, MS’ lawyers would probably come after him at the first glance of a red/green/blue/yellow button that looks remotely similar to the Windows logo on the start button of Windows 7.
But don’t fret. Nir Sofer has a nice tool called ResourcesExtract which we can use on Windows 7 to get to the start button bitmaps, like this:
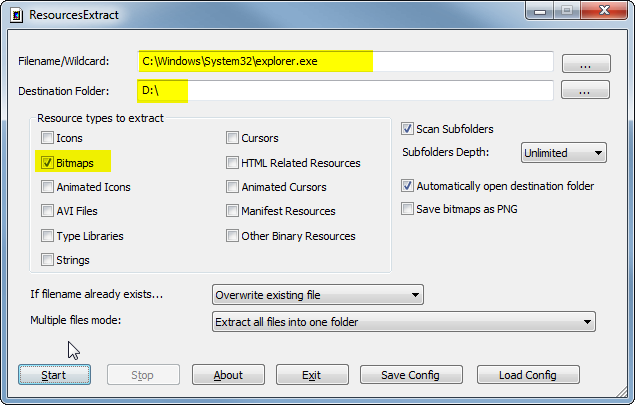
You’ll only want bitmaps and you only need to look inside explorer.exe in the path given in the screenshot.
The resource IDs of the bitmaps you’re looking for are:
- 6801, 6802, 6803, 6804
- 6805, 6806, 6807, 6808
- 6809, 6810, 6811, 6812
They are grouped in three groups of four, because there are indeed three styles of the start button that differ very very slightly. A good diff program can show the differences, so if you’re curious try that. Pick one of the groups and you get four different sizes where each size contains three vertically stacked start buttons. The upper one is the default look. The middle one is the look when you hover over the button and the lower one is the look when you click (and hold) the button.
ClassicShell’s classic start menu is well capable of handling this format of bitmap. Best of all you can convert it to a PNG file to save a few KiB of disk space and store it on the target machine: Windows 8, 8.1 or Server 2012, Server 2012 R2. Select it from the Classic Start Menu settings:
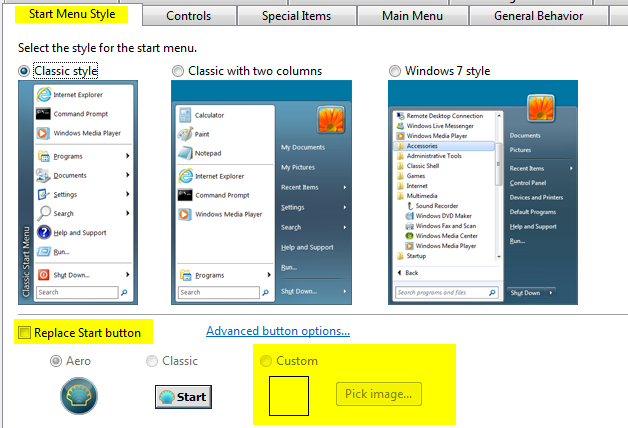
Btw: the first choice on the left is the ugly (sorry Ivo 😉 ) start menu style I mentioned at the beginning.
For obvious reasons I cannot show you the result, since I cannot afford an email from MS’ legal department 😆
// Oliver
PS: also check out the other great tools on Nir Sofer’s website!



